Pretty much everyone has heard of the terms spyware, malware, virus, trojan horse, computer worm, rootkit, etc, etc, but do you really know the difference between each of them? I was trying to explain the difference to someone and got a little confused myself. With so many types of threats out there, it’s hard to keep track of all the terms.
In this article, I’ll go through some of the major ones we hear all the time and tell you the differences. Before we get started, though, let’s get two other terms out of the way first: spyware and malware. What’s the difference between spyware and malware?
Spyware, in it’s original meaning, basically meant a program that was installed onto a system either without your permission or clandestinely bundled with a legit program that collected personal information about you and then sent it off to a remote machine. However, spyware eventually went beyond just computer monitoring and the term malware started to be used interchangeably.
Malware is basically any type of malicious software intended to do harm to the computer, gather information, gain access to sensitive data, etc. Malware includes viruses, trojans, root kits, worms, keyloggers, spyware, adware, and pretty much anything else you can think of. Now let’s talk about the difference between a virus, trojan, worm and rootkit.
Viruses
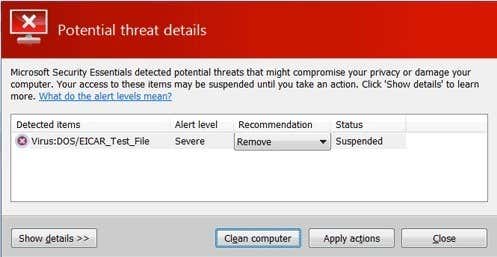
Even though viruses seem like the majority of malware you find these days, it’s actually not. The most common types of malware are trojans and worms. That statement is based off the list of top malware threats published by Microsoft:
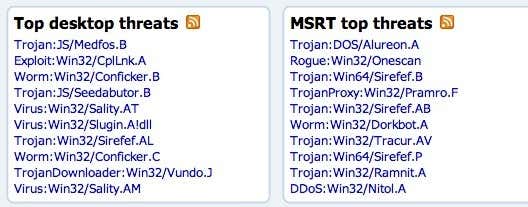
So what is a virus? It’s basically a program that can spread itself (replicate) from one computer to another. The same is true for a worm also, but the difference is that a virus usually has to inject itself into an executable file in order to run. When the infected executable is run, it can then spread to other executables. In order for a virus to spread, it normally requires some kind of user intervention.
If you have ever downloaded an attachment from your email and it ended up infecting your system, that would be considered a virus because it requires the user to actually open the file. There are lots of ways viruses cleverly insert themselves into executable files. One type of virus, called a cavity virus, can insert itself into used sections of an executable file, thereby not damaging the file nor increasing the size of the file.
The most common type of virus nowadays is the Macro Virus. These are sadly viruses that inject Microsoft products like Word, Excel, Powerpoint, Outlook, etc. Since Office is so popular and it’s on the Mac too, it’s obviously the smartest way to spread a virus if that’s what you’re looking to accomplish.
Trojan Horse
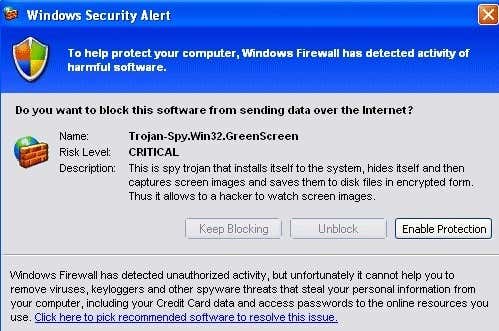
A Trojan Horse is a malware program that does not try to replicate itself, but instead get installed onto a users system by pretending to be a legitimate software program. The name obviously comes from Greek mythology since the software presents itself as harmless and thereby tricks the user into installing it on their computer.
Once a Trojan Horse gets installed on a user’s computer, it doesn’t try to inject itself into a file like a virus, but instead allows the hacker to remotely control the computer. One of the most common uses of a computer infected with a Trojan Horse is making it part of a botnet. A botnet is basically a bunch of machines connected over the Internet that can then be used to send spam or perform certain tasks like Denial-of-service attacks, which take down websites.
When I was in college back in 1998, one crazy popular Trojan Horse at the time was Netbus. In our dorms, we used to install it on each other’s computers and play all kinds of pranks on each other. Unfortunately, most Trojan Horses will crash computers, steal financial data, log keystrokes, watch your screen with your permissions and lots more devious stuff.
Computer Worm

A computer worm is just like a virus, except that it can self-replicate. Not only can it replicate on it’s own without needing to a host file to inject itself into, it normally also uses the network to spread itself. This means that a worm can do serious damage to a network as a whole, whereas a virus usually targets files on the computer that is infected.
All worms come with or without a payload. Without a payload, the worm will just replicate itself across the network and eventually slow the network down because of the increase in traffic caused by the worm. A worm with a payload will replicate and try to perform some other task like deleting files, sending emails, or installing a backdoor. A backdoor is just a way for to bypass authentication and get remote access to the computer.
Worms spread primarily because of security vulnerabilities in the operation system. That’s why it’s important to install the latest security updates for your OS.
Rootkit
A rootkit is malware that is extremely hard to detect and that actively tries to hide itself from the user, the OS and any anti-virus/anti-malware programs. The software can get installed in any number of ways including exploiting a vulnerability in the OS or by gaining administrator access to the computer.
After the program has been installed and as long as it has full administrator privileges, the program will then go about hiding itself and altering the currently installed OS and software to prevent detection in the future. Rootkits are what you hear will turn off your anti-virus or install into the OS kernel, whereby your only option sometimes is to reinstall the entire operating system.
Rootkits can also come with payloads whereby they hide other programs like viruses and key loggers. To get rid of a root kit without reinstalling the OS requires users to boot to an alternative operating system first and then try to clean the rootkit or at least copy off critical data.
Hopefully, this short overview gives you a better sense of what the different terminology means and how they relate to each other. If you have something to add that I missed, feel free to post it in the comments. Enjoy!

